As a business, you want your goods transported reliably and safely. They go through great lengths for goods to not be lost or damaged on their way. But how secure and safe is your software? And how do you ensure the goods arrive as promised? The security of your software is just as vital for your business as the security of your goods is. Just as you do not want to lose any physical cargo, we do not want your data to be lost or handled in an unsafe way.
Security is one of the main priorities. We make sure that your software security is at its best in various ways:
Secured connections
APEX-SERT
A super safe hosting environment
Minimal access to the servers
Daily back-up
Tenants
IP-filtering
User management
Two factor authentication
Secured connections
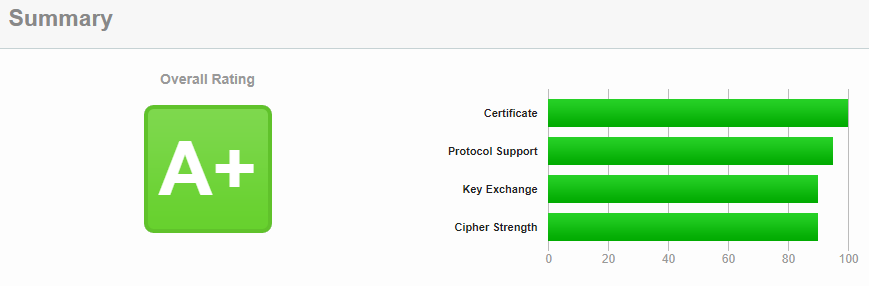
All of our software is available in the cloud. As a result, all the software is accessible by an internet browser. To safely work within a cloud-based environment, a secured connection is needed. Adaption software runs on an encrypted connection. In other words, an SSL certificate. GlobalSign publishes these certificates. They are one of the most reliable publishers of SSL certificates. Companies like Ford, Toyota, Netflix, Microsoft and BBS use these SSL certificates. Feel free to take a look at the website of SSL labs.
APEX-SERT
Another safety measure we’ve taken is the implementation of APEX-SERT into our development and testing process. This tool evaluates applications on several security risks and identifies any vulnerabilities. APEX-SERT is fully integrated into the application builder, the developing software we use to develop our software. Many companies are using APEX-SERT after developing software to evaluate the software. We use it differently. APEX-SERT is a part of our developing process, and our APEX-SERT checks every environment on possible threats every night. After the checks, we receive a status mail with issues regarding the security standards. If there are any issues, we immediately fix the reported issues. To ensure the safety of our customers’ software we only release it when the score is 100%. Our goal is to maintain this percentage of excellence.
A super safe hosting environment
Adaption has a server in an exceptionally secured hosting environment. The server is part of a data centre at Schiphol, with the nickname “The Bunker”. The data centre fully complies with European legislation and even surpasses it.

Firewalls
Multiple internet connections and redundant firewalls make sure that there is connectivity with the outside world. The entire environment is based in the state-of-the-art data centre of Equinix on the Amstel Business Parc. The servers are located in one of the best data centres of the Netherlands: TeleCity 4 – Amstel Business Parc, and the backup is located in TeleCity 5, both in Amsterdam. The locations are connected with a double 10Gbe ring (20Gbe throughput).

ISO standards
The data centre takes care of the potential environmental hazards (security, fire, power). This server environment is monitored continuously for potential threats. The facilities meet the international standards of ISO 9001: 2008 for quality, OHSAS 18001:2007 for security, ISO/IEC 27001:2005 for information security and PCI-DSS, chapter 9 for vulnerability.

Virtual Machine
It is almost impossible for someone to enter our hosting environment. All the spaces are conditioned and protected from fires, power loss and water damage. The physical server of Adaption runs on a Virtual Machine that runs on a shared hard drive by RAID. Because of this, we created a fallback scenario of five minutes. If the server crashes, another server is up within five minutes.
Daily back-up database
Every night a backup of all data is made and saved for 30 days. The backups are kept off-site, in another secured area. Due to the off-site backups, we can guarantee your backup data is never lost.
IP-Filtering
Working in the Cloud has many advantages. One of them is that the software is available at all times, from any location and through supported every device. However, sometimes users shouldn’t have access to sensitive information. It is possible to allow users access from a predefined list of IP addresses.
Minimal access to the servers
We use a proxy server that avoids attacks like cross-side scripting. Cross-side scripting is an error in the security of a web application. Input processed faultily is the cause of this error. A cookie or URL request may cause these faulty inputs. All other webservers and databases are closed for the outside world. There is no other possibility to reach this data than through this proxy server.

User management
Within the application, different roles can be defined. A role determines which pages, processes and reports are allowed to be executed. For example, you can define that your transport planner can’t edit or see the invoicing area or the employee administration. Another option is that a certain user has the right to see data, but not to edit the data. A user can have one or multiple roles.
Tenants
All of the logistic software products of Adaption are Cloud solutions. To ensure that all your data is perfectly secured, we use tenants. A tenant is a separated user environment that is configurated for the user. Do you have multiple departments or companies, and do you want to use the same software? A leading tenant with various companies or departments configured under that tenant would be a possible solution. All the master data, like scenarios, will be shared, but, for instance, orders, quotations and invoices are shown accordingly.
Two-factor authentication
You can log into all our software solutions in two ways: via username and password or a two-phase login. The two-phase login is an addition to logging in via the username and password. After the first login step, the user sees a code on their smartphone. They must then enter this information in the second login screen. We use the TOTP, a Time-based One-time Password algorithm, for this method.

More information?
Do you want to know more about our software security policy and measures?
Do you want to take a look at our products?



